Cybersecurity for ships
The situation of basic guidelines for implementing cybersecurity for ships has become much better when Code of Practice: Cyber Security for Ships was published 2017 by the Institution of Engineering and Technology. This important guideline declares the basic management framework to lower the probability of cyberattacks against different types of ships.
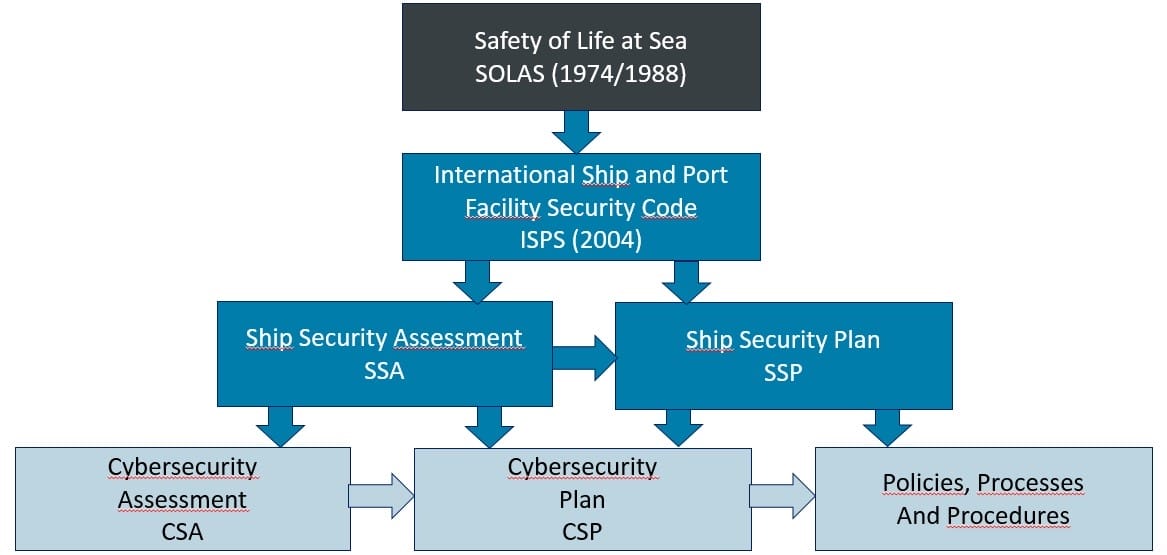
The most recent components in the evolution of the management framework of cybersecurity for ships are the CyberSecurity Assessment CSA and CyberSecurity Plan CSP. A new Cybersecurity Officer CySO has task to develop, review periodically and maintain both CSA and CSP.
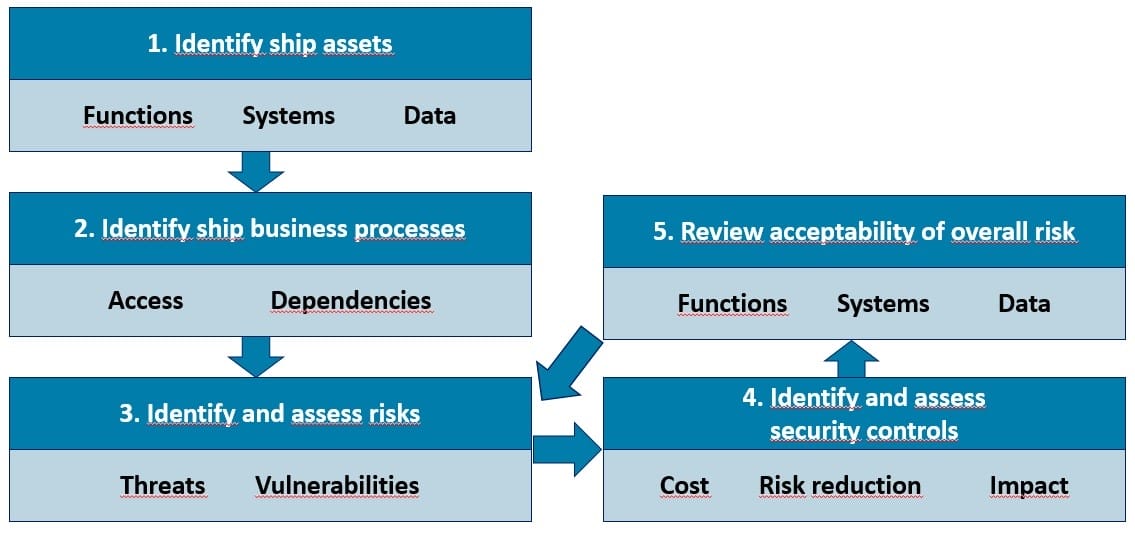
The Cyber Security Assessment CSA is based on a risk management approach. The cyber security risks are prioritized to mitigate the vulnerabilities in cost-effective ways. In the CSA process, the ship assets, the ship business processes, the ship risks and security controls needed are identified. The review of the CSA should be done frequently according rapidly changing cybersecurity situation.
A comprehensive approach for developing the Cybersecurity Plan CSP is also important to cover all the areas of cybersecurity. The CSP should cover all the policies, processes coming from the policies and procedures to give more detailed directions to cybersecurity. The CyberSecurity Plan CSP should be based on the CyberSecurity Assessment CSA and it covers the three security levels of the ISPS Code, which are minimum appropriate, appropriate additional and specific protective security measures.
For example, here are some of very minimum contents of a Cyber Security Plan CSP for ships to cover:
- responsibilities
- approving connections to ship systems
- changes to system operations
- access and control to communications and navigation systems
- access and control to IT and OT systems
- access and control to electronic monitoring systems
- protection of data concerning cargo and stores
- response to threats, breaches and cybersecurity incidents
- auditing of cybersecurity controls
- links to assisting organizations
- awareness, training and drills required by personnel
Building upon these aspects, we can expect to improve the security of the ship, its crew, passengers and cargo.
References
Code of Practice: Cyber Security for Ships. 2017. London, UK: Institution of Engineering and Technology.
Kohnke, A., Shoemaker, D. & Sigler, K. 2016. The Complete Guide to Cybersecurity Risks and Controls. Boca Raton, FL: CRC Press.